Image Source: Time to Break.
Digital home invasion. Stick that Post-it over your laptop camera, because here is a real life premise for a found footage film if I ever saw one. In July 2015, a hacker sent a woman in Toronto, Canada photos of her sleeping with her partner, taken through the camera of her boyfriend's computer. Police were unable to protect the couple after the captures were posted on her Facebook account. VICE:
Also in July 2015, a Canadian man heard an eerie voice screaming obscenities and shouting "Wake up baby! Wake up baby!" at his infant child. The voice came from the hacked baby monitor in the nursery. In late 2014, several reports noted that a Russian-based Website, Insecam, streamed thousands of hacked security cams and Webcams in the USA, UK, Canada and Australia. These articles fine tuned the growing paranoia that nothing on the Internet is private.It was the end of a long day, and Chelsea Clark and her boyfriend had settled in for a Netflix marathon on his laptop. "We were for sure watching Adventure Time," says the 27-year-old bartender. "Pretty normal Wednesday night stuff." Yet the couple's rather unremarkable, rather intimate evening soon became anything but.Logging into Facebook after work the next day, Clark says her blood ran cold. An anonymous account had sent her a series of photos of the couple's evening, seemingly taken from the laptop's camera. "They were so freakishly intimate," she says."Realy,cute couple [sic]" was the only message.Terrified, Clark immediately called the Toronto police. "It felt so invasive, like someone was in my house with me." ...
The images were taken using her boyfriend's PC laptop, a computer Clark says she never uses. "It's just for video games and occasionally we'll use Netflix on it," she explains. From there, the perpetrator managed to make the link to Clark, hacking into her Facebook account and adding himself to her contacts to send the images. "I have my privacy setting set so that no one can message me except friends," she says of her Facebook account. "So when I got an unknown [message] I thought it seemed weird," she says. "I went into history to see when [the user] was added and it was just before the messages were sent."Cyber security expert Eric Parent says the context suggests the perpetrator knows the couple. "Or we're dealing with someone who took the time to understand the relationship between these two people," says Parent. "And that takes digging, since it's not because I saw you on a webcam that I know who you are."The (now-deleted) Facebook profile used to send the photos offers little insight into the perpetrator's identity (Mahmoud Abdo seems to be an incredibly common name, and is likely a fake). Alongside profile pictures featuring Heath Ledger as the Joker or strange motivational sayings, the person followed a variety of soccer club pages and belonged to a group called "Spammers and Hackers." The user's location is listed as Cairo, Egypt. ...
Parent warns that hacking a webcam is relatively easy. "If you have access to the physical computer, all you need is some tech knowledge and a USB key and you're done," he says. Remote access, he explains, requires some form of user involvement. "Something has to be clicked, a doc has to be opened," he says. But all in all, it's a relatively simple hack that can be hard to detect. "It's very difficult to protect yourself from this type of attack because the stuff that we do normally, like opening email, is stuff that just happens," says Parent. "The best thing you can do is to have security software, keep everything up to date, and cross your fingers."
"Watching a young girl in Malaysia. Note RAT [Remote Administration Tool] control center running in background." Image Source: Ars Technica.
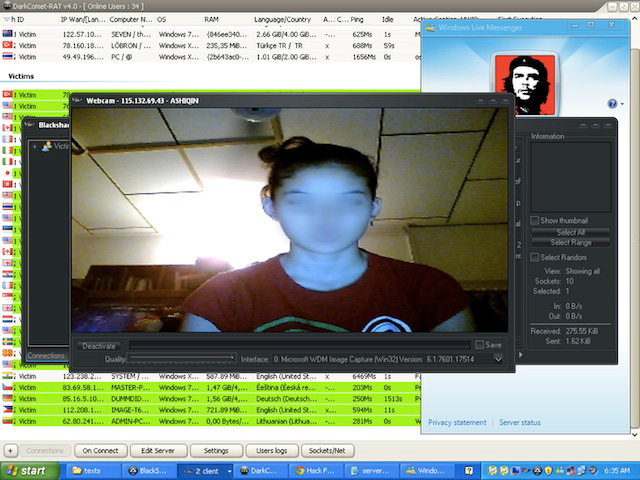
It takes more than a Post-it note, because hackers depend on invasive malware, easily found on the Dark Net or Deep Web. Webcam spy software was developed over the past five years during the Syrian crisis as the government there sought to spy on rebels and ISIS fighters. In March 2014, The Intercept argued that the vulnerabilities in personal computers are not addressed because they suit corporate and government spies, and hackers simply benefit on the side. But would-be hackers don't even have to be so adventurous. Several Youtube videos advise beginners, and a startling example in this 2011 Youtube video, warns: "I discovered a vulnerability in Adobe Flash that allows any website to turn on your Webcam and microphone without your knowledge, to spy on you." Male hackers spy on women through their laptop and desktop cameras using a Remote Administration Tool, or RAT. This tool spawned a sub-culture of 'ratters'; some are bored and emotionally challenged, but Digital Citizens' Alliance reported in July 2015 on dedicated ratters who sell bundles of information on women's hacked cameras; the most malevolent ratters inspired a 2015 film. In March 2013, Ars Technica reported:
The woman is visible from thousands of miles away on a hacker's computer. The hacker has infected her machine with a remote administration tool (RAT) that gives him access to the woman's screen, to her webcam, to her files, to her microphone. He watches her and the baby through a small control window open on his Windows PC, then he decides to have a little fun. He enters a series of shock and pornographic websites and watches them appear on the woman's computer.The woman is startled. "Did it scare you?" she asks someone off camera. A young man steps into the webcam frame. "Yes," he says. Both stare at the computer in horrified fascination. A picture of old naked men appears in their Web browser, then vanishes as a McAfee security product blocks a "dangerous site.""I think someone hacked into our computer," says the young man.Far away, the hacker opens his "Fun Manager" control panel, which provides a host of tools for messing with his RAT victims. He can hide their Windows "Start" button or the taskbar or the clock or the desktop, badly confusing many casual Windows users. He can have their computer speak to them. Instead, he settles for popping open the remote computer's optical drive.
Hacked footage from baby monitors appeared on the Russian Website, Insecam. The site closed after reports attracted public attention. Image Source: Crave Online.
"Using a RAT to scare a victim is another favourite of the hackers - as well as taking content they can flash content up on the screen of the machine they have accessed." Image Source: Daily Mail.
"A woman unknowingly captured by her own webcam." Image Source: Ars Technica.
Spies discuss their crimes on private underground chat sites as well as the more public Hack Forums, where they call their victims "slaves":
A hacker can take over a targeted computer completely, turning it into a bugging device even when the machine is offline. 'Sextortionists' manipulate a mark using stolen private files, or video and audio captured from the victim's room. They can hear conversations, track down telephone numbers, addresses and banking information; sometimes posing as a victim's boyfriend, they request nude photos and then blackmail the target. One such case occurred in Los Angeles in 2009, in which the FBI Cyber Squad finally caught hacker Luis Mijangos, but not before he had done a lot of damage:a 134+ page thread [is] filled with the images of female "slaves" surreptitiously snapped by hackers using the women's own webcams. "Poor people think they are alone in their private homes, but have no idea they are the laughing stock on HackForums," he continued. "It would be funny if one of these slaves venture into learning how to hack and comes across this thread."
Young girls are particularly vulnerable. In India, women have been targeted in vicious attacks all over social media and through computer hacks. Law enforcement offices across the USA have noticed a rapid rise in sextortion of teen girls. In 2014, Miss Teen USA, Cassidy Wolf, was targeted by a sextortionist who hijacked her Webcam; she took the threats to the police and the ratter was convicted and imprisoned. Wolf subsequently toured high schools to explain this growing problem to students.[A] Los Angeles area juvenile named Sara received an instant message from a screen name that looked almost identical to her boyfriend's. The person behind it asked her for pornographic photos; she supplied them. She soon realized her mistake, but it was too late. Threats began to roll in, saying that her mysterious interlocutor would post Sarah's nude photos on the Internet if she did not send more. When Sara e-mailed copies of these threats to her boyfriend, the stalker knew. He even called her on the phone to make the threats more personal. ...The FBI [later] found different kinds of malware on the [hacker's] computers, including tools to install a key logger on remote machines, software to turn on webcams and microphones attached to infected computers, and "dozens of videos" from those webcams, most showing the victims " getting out of the shower, dressing for the day, having sex with a partner.”In a file called "things importan" [sic], the FBI even found screen captures from victim machines showing identifying information about them displayed on bank and financial websites.
NBC report on Miss Teen USA sextortion case (2014). Video Source: NBC via Youtube.
CNN Interview with hacking victim Miss Teen USA Cassidy Wolf (2014). Video Source: CNN via Youtube.
Vimeo Awards Short Film Finalist: Webcam (2012) by ZBros Productions/ Stefan Haverkamp/ Jan Jaworski/ Branden Kramer/ Tom Kropp, a fictionalized version of a 2009 Los Angeles computer camera hack. Video Source: Vimeo.
Some malware pretends to mimic police cybercrime apps. More information:
- FBI's cybercrime most wanted list is here
- National Cyber Crime Unit of the UK is here
- Canadian RCMP's cybercrime page is here
- Centre for Cyber Victim Counselling, India
- Computer Misuse Act, Singapore
- Europol European Cybercrime Centre
- Interpol Global Complex for Innovation
- Digital Citizens' Alliance (July 2015): "Selling Slaving: Outing the Principal Enablers that Profit from Pushing Malware and Put Your Privacy at Risk"
- The Atlantic (23 December 2014): "The Webcam Hacking Epidemic"
- Info Security (2 September 2014): "Cybercrime and Punishment"
See all my posts on Ghosts.
Check out other blogs observing the Countdown to Hallowe'en!
























No comments:
Post a Comment